5 Myths About Android Security: VPN, Antivirus, Password Managers, Rooting
Dawn of indisputable trust to the magic of security software.

Top 5 Myths
Myths #1: About Using VPN
Myths #2: About Password Managers
Myths #3: About Antivirus
Myths #4: About Rooting a Device
Myths #5: De-Googling
Top 3 Advice
Advise #1: Don't Trust Anyone
Advise #2: Update Often
Advise #3: Use Strong Authentication
Preface
I love to find conflicting claims inside a single post. Let's see what is going on in the article "11 Android security tips" at bestvpn.com. There is a tip that suggests installing apps from a custom app store (e.g. Android Drawer), and this implicitly implies turning on a "Settings > Security > Unknown Sources" option. The second tip is about denying applications from unknown sources, and this explicitly implies turning off the "Unknown Sources" option. You see, "on" versus "off" in the same list.
I'm going to walk through "11 Android security tips", "10 Android phone security tips you need to know", these tips, and a few similar ones.
I stay against the ultimate pitching of the "best" security practices that mislead users.
I encourage critical thinking.
I will talk in detail about security basics and the problem of trust.
Myths #1: About Using VPN
📰 "Use VPN to stay secure. Avoid insecure connections."
There is nothing bad in advice to secure connection, but we are talking about Android security, right? There is a little bunch of nuances related to VPN in the context of privacy.
So, what's wrong with that?
1. VPN collects private data, then private data can be transferred to third parties
There is a gigantic investigation discovering free VPN providers, a lot of them are secretive companies with Chinese ownership: "Free VPN Apps: Chinese Ownership, Secretive Companies & Weak Privacy".
Another news spots data theft from a hacked VPN provider: "VPN Provider Citrix Hacked, Up to 6TB of Data Accessed".
A modern VPN service acts like a pumped proxy server.
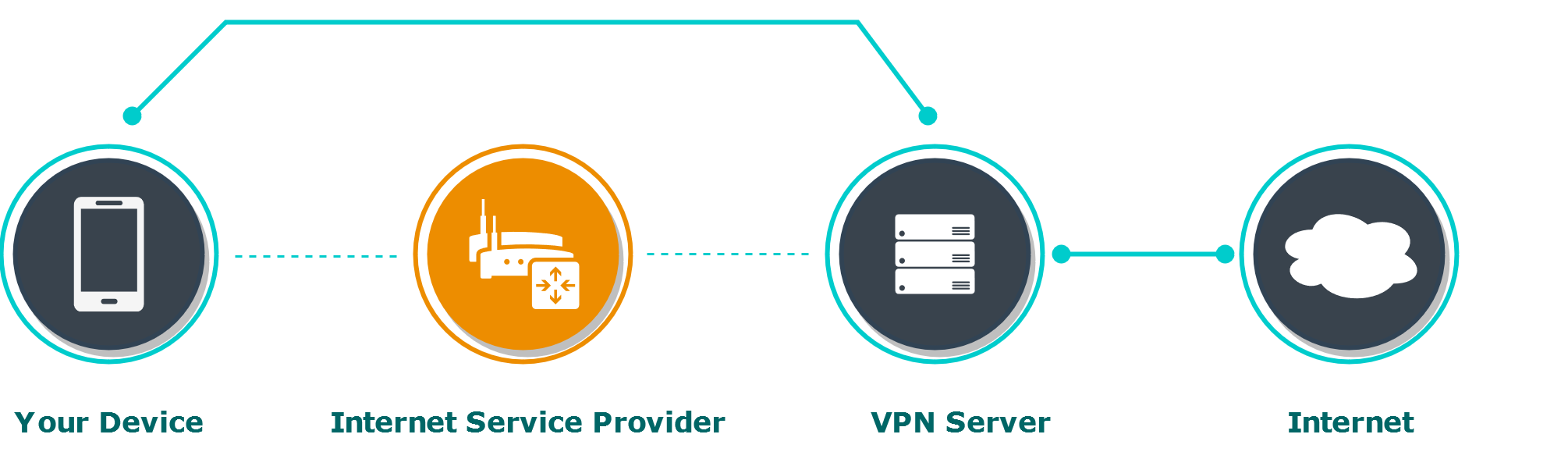
The amount of collected private data, the level of data protection, and the level of misuse, depend on the particular VPN that a customer decides to use. Unreliable companies may leak your private statistics, other ones improperly protect collected information.
Therefore, customers should be wise to choose a VPN provider. You cannot just go to the Google Play store and use any randomly selected VPN appearing there in a list.
2. Disconnect your device to stay more secure
There is a simple principle:
| Device is disconnected | Device is connected |
|---|---|
| Device is more secure | Device is less secure |
There is a trade-off between being online and being secure.
Why so? Because once you are in the network, your private data leaks: DNS requests, unencrypted data exchange, hidden application usage statistics, and device usage statistics. You're taking back the phishing emails, scam, viruses, and adware.
The safest system is a vault underneath the ground.
3. VPN is for network security and Internet freedom
VPN can secure your Internet experience. VPN leverages your Internet freedom, and I like that concept. It allows for bypassing government and ISP restrictions.
Still, VPN is a case of network security, not really about Android device security. Of course, once you are on the web, you need to balance between comfort and safety. VPN is the point, however, we face a concept of trust.
4. Shifting a point of trust toward VPN
If you decided to use VPN, choose a VPN vendor you're going to trust. Think twice. Be careful.
Eventually, once you are connected, data starts transferring, and now the VPN vendor is a single point of trust that may collect all the data from your device. The Internet service provider (ISP) doesn't see your steps on the web, but the VPN server does. (The VPN provider may see your DNS requests, a target website, and basic behavior during the session, however, using HTTPS for surfing websites doesn't show the actual data to the intermediary servers as the channel is encrypted on top of the VPN connection).
Whom would you trust? Are you sure that a VPN vendor doesn't sell data collected about you to any third parties? Who is the owner of a concrete VPN?
Check information about the supposed VPN provider in the article "Free VPN Apps: Chinese Ownership, Secretive Companies & Weak Privacy".
If you're confused to choose a relatively reliable VPN provider, check recommendations on the Internet.
If you're still not sure, don't enable VPN. Don't forget to check HTTPS in the address bar of the browser and consider basic precautions.
Myths #2: About Password Managers
📰 "Password manager is a way to generate and manage strong unique passwords. Therefore password manager improves your security."
1. Brain is the most secure place for a password
A strong unique password is a good deal for sure. Don't confuse it with a strong password manager.
Security is getting worse starting at the moment when a third-party application takes care of your secrets synchronizing them over the Internet.
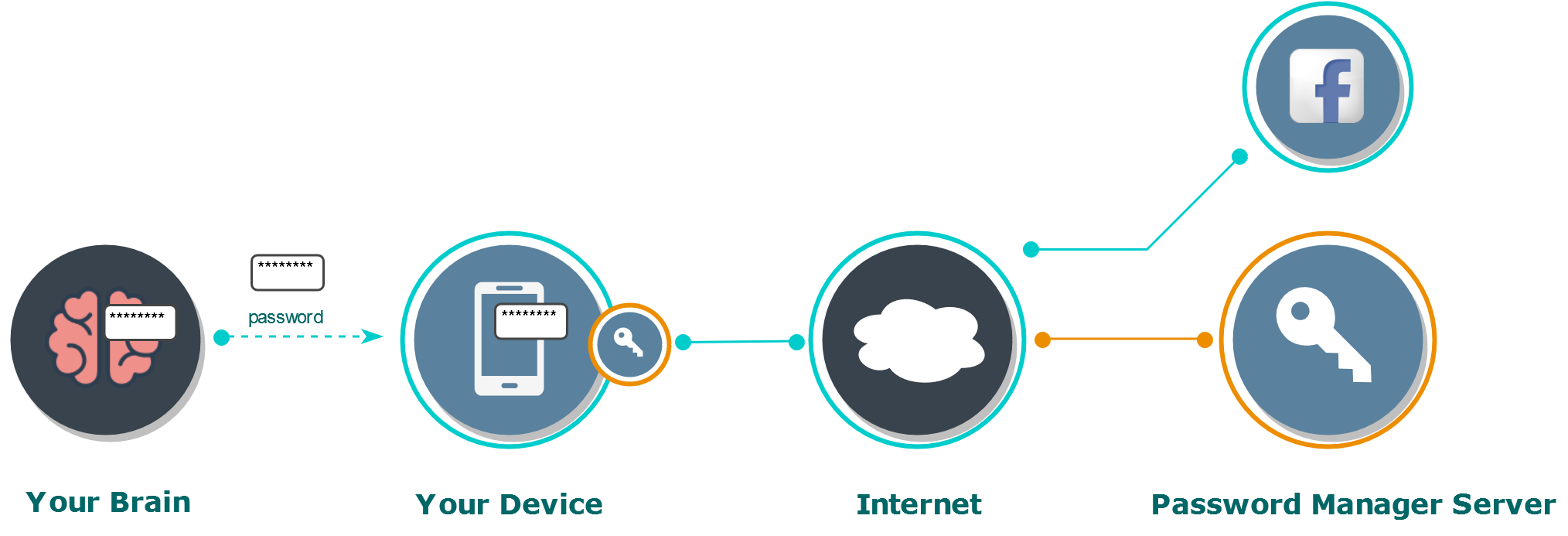
A password manager is a custom third-party software. A good password manager encrypts your password before transferring it over the network. All passwords are usually encrypted on a single master password. Periodically passwords are synchronized.
The main question: does a particular password manager deserve trust? Is a concrete password manager free from leaks and critical vulnerabilities?
A single vulnerability leads to compromising the entire set of passwords.
2. Password manager is less about security, it's more about user experience
It's hard to create a new password for each account, and it's hard to remember them all. A password manager helps you with generating new passwords, encrypting all passwords on a single master password, and synchronizing over the network. A password manager makes the user experience smoother.
Do you remember: we are talking about security.
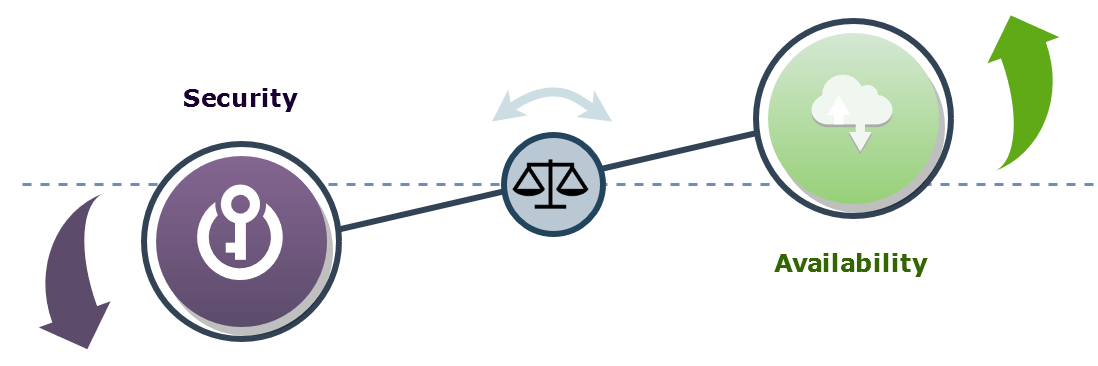
Recall the "security versus availability" dilemma.
The brain is secure but not reliable. You can forget a complex password, then your private data turns out to be encrypted forever, your account gets closed, and it's all sad. But everything remains secure. Secure but not available.
A password manager is the opposite case. It reliably controls many passwords, but you should trust a password manager to give up all the responsibility.
| Password in your head | Password in a password manager |
|---|---|
| Security is better | Security is worse |
| Availability is worse | Availability is better |
3. Choose a strong password that you can remember
A strong password is not always that is hard to remember.
A phrase of few words could be much stronger than a complex pseudo-random password. I love the comics on https://xkcd.com/936/.
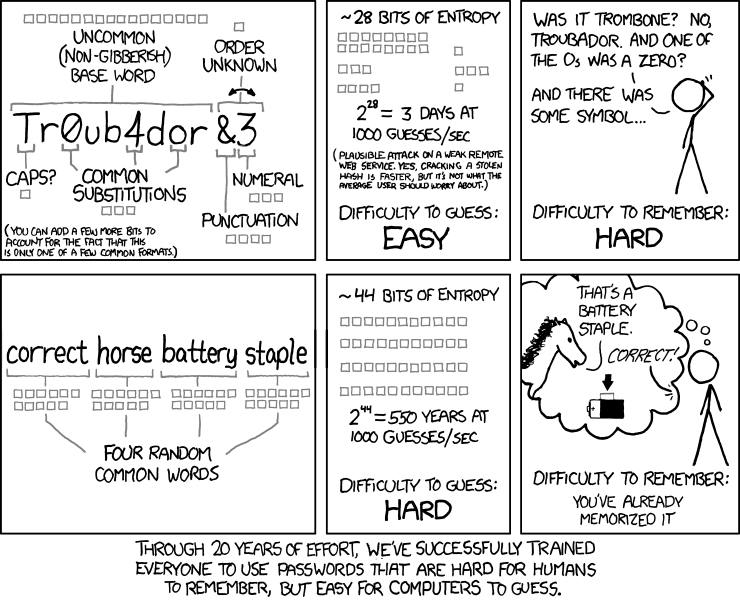
Note, that a password manager generates a password that should be properly randomized but really hard to remember.
4. What password manager would you trust?
Consider a pretty generic situation: you try to log in to any website.
| Before | After |
|---|---|
| You enter a password | Password manager enters a password |
Be careful. Choose a password manager carefully. If you're not sure: don't install a password manager and remember strong passwords by yourself.
Myths #3: About Antivirus
1. With great power comes great responsibility
Modern antivirus software is more than a file checker, it may contain anti-phishing, anti-theft and other protections. And it's good news.
Modern antivirus software is a cloud-based technology with wide access to files and system resources. And it's a "so so" news.
A user installs a custom application, i.e. antivirus app, and that application gets incredible power because the user allows all possible permissions ever existed.
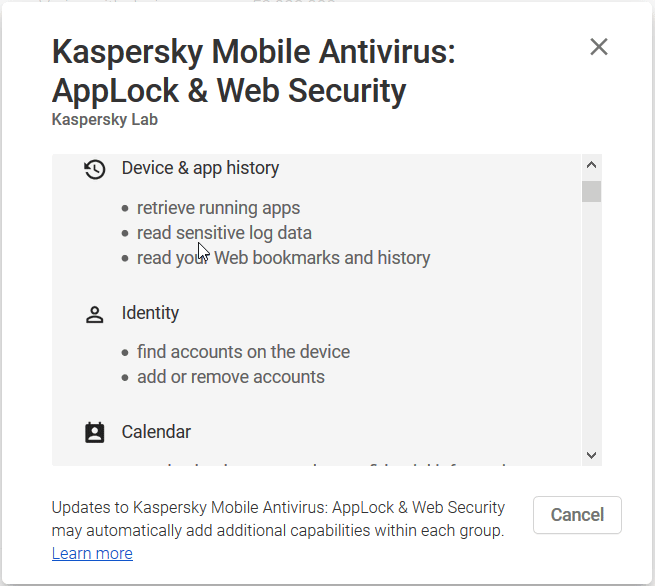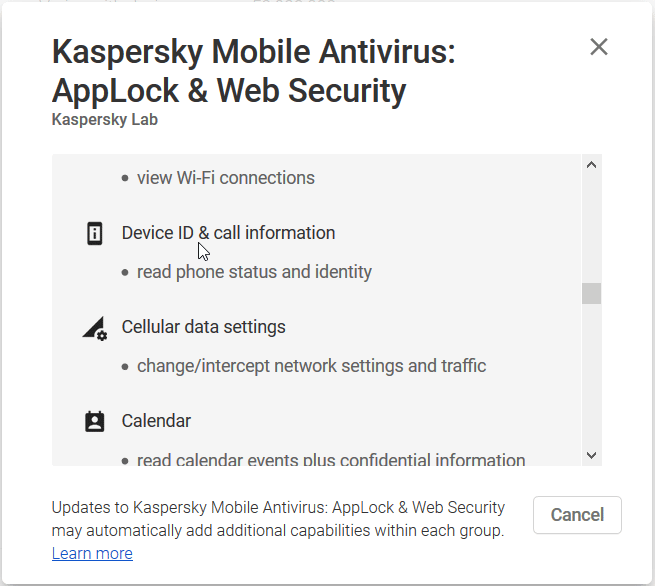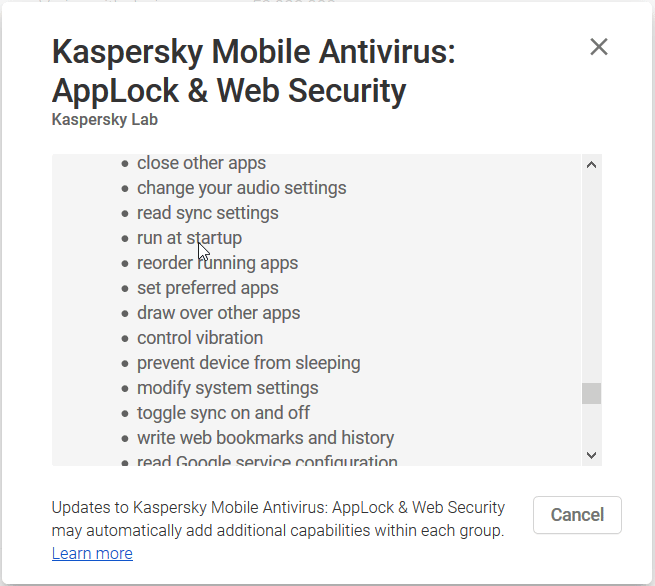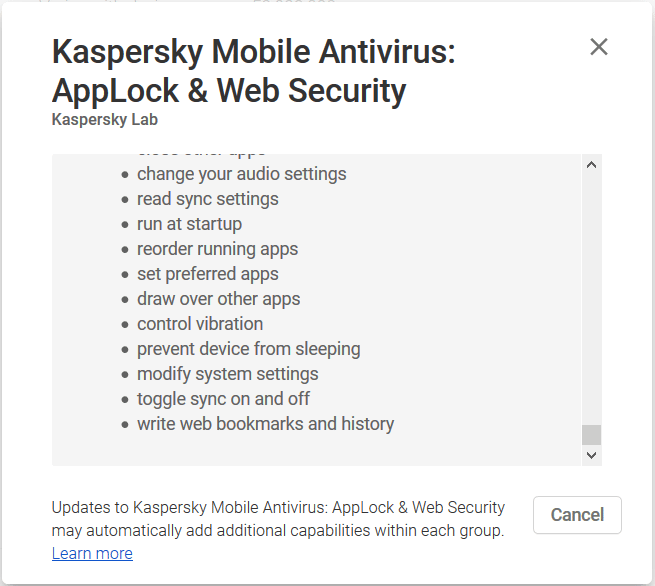
You can expect at least 2 undesirable consequences then:
- Unreliable antivirus software may collect private information and send it via the Internet.
- If an antivirus app is hacked, then someone gains access to all collected information.
Another bad news is that Most Android Anti-Malware Apps Don’t Offer Any Protection.
2. The best antivirus doesn't exist
There is no antivirus/anti-malware application able to catch all viruses and magically solve security issues.
As well as there is no VPN able to magically solve all network security issues.
"Antivirus versus virus" is an endless game. Once a new virus spreads over the Web, it makes harm until its signatures are added to the antivirus database and populated among the customers.
3. Don't install applications from unknown sources
The current concept of Android mobile devices is that you install applications from a trusted source (e.g. Google Play), where the application is already verified about viruses.
Antivirus itself is verified in Google Play against viruses and well-known malicious patterns, but there is a problem to verify all internal logic and protocols.
If you really need more security services, then care about what antivirus to trust.
Myths #4: About Rooting a Device
📰 "Superuser allows making devices more secure via installing powerful security tools and early Android updates. After rooting you can tune up your Android system, remove ads, improve performance, and hack the games for a sake of adventures."
1. Superuser is too powerful
Android applications are isolated from each other (basically via unique UID/GUID), but an application with root privileges has the power to read/write into another one.
2. Malware + root = love
When the superuser is enabled then malware has a precious gift. Malware can use root to go into each application, get secret keys and disclose sensitive personal data.
A lot of good points could be found in Kaspersky's Blog: "Rooting your Android: Advantages, disadvantages, and snags".
After gaining superuser access rights, malicious applications enjoy full freedom. In fact, the first thing many Trojans for Android do is attempt to gain root access. Users rooting their own devices offer quite a gift to malware developers.
Myths #5: De-Googling
📰 "Remove Google Services because Google spies."
1. De-Googling implies rooting
Root privileges must be gained to remove Google Services. While it's not recommended to enable root. See Myth #3: Root a Device to get that rooting is the worst security advice ever.
2. "Unknown sources" must be allowed
A third-party app store would be used instead of removing Google Play. It implies enabling the "Unknown sources" option in Android settings which may harm the security of Android.
3. And about a trust
Getting back to the problem of trust.
Obviously, advice to remove Google Services derives from a point of not trusting Google which collects hidden statistics of different granularity.
Advice: rely on the ecosystem, and change the ecosystem in the opposite case.
Google invests a lot in Android security. As well as Apple into its own ecosystem. Google Play Store is being improved continuously including malware and malicious behavior detection. Check the Android Treble Project which brings modularity and a lot of security hardenings into Android starting from Android 8.0.
Rooting and customizing Android without deep expertise is rather harmful.
Talking about Android Drawer the best security feature there is that mostly all apps have been taken from Google Play. Unfortunately, Android Drawer allows submitting third-party applications avoiding Google Play.
Choose carefully whom you will trust.
Top 5 Advises to Keep Android Secure
Keep It Simple Stupid
Let me cut the long story short. You just need to be careful and don't act way much proactively.
Let me share my personal chart of the best security tips.
Advise #1: Don't Trust Anyone
- Don't install apps from unofficial sources.
- Check permissions before app installation.
- Be careful in the web.
- Check HTTPS in the address line.
- Watch out phishing emails.
Advise #2: Update Often
System updates contain security patches. Sometimes new bugs. But more likely security patches.
- Update Android.
- Update applications.
Advise #3: Use Strong Authentication
- Secure your device:
- lock it down
- don't use 1234 as your PIN
- Secure your accounts:
- enable 2-factor authentication
- don't use simple password