Application Security with OWASP ASVS
OWASP ASVS is a comprehensive check list of application security. You go through the check list, assess a software, report to stakeholders, improve security. OWASP ASVS is a superset of PCI DSS and OWASP Top 10.

Short Formula
OWASP ASVS = check list of application security

You go through the check list and... check the security of your software.
Overview
OWASP ASVS (Application Security Verification Standard) is a guide to assess an application or a platform: secure payment, healthcare, business application. You need a plan, a way to start, and to get practical outcomes.
PDF: OWASP Application Security Verification Standard 3.0.1.
OWASP ASVS is a superset of PCI DSS and OWASP Top 10:
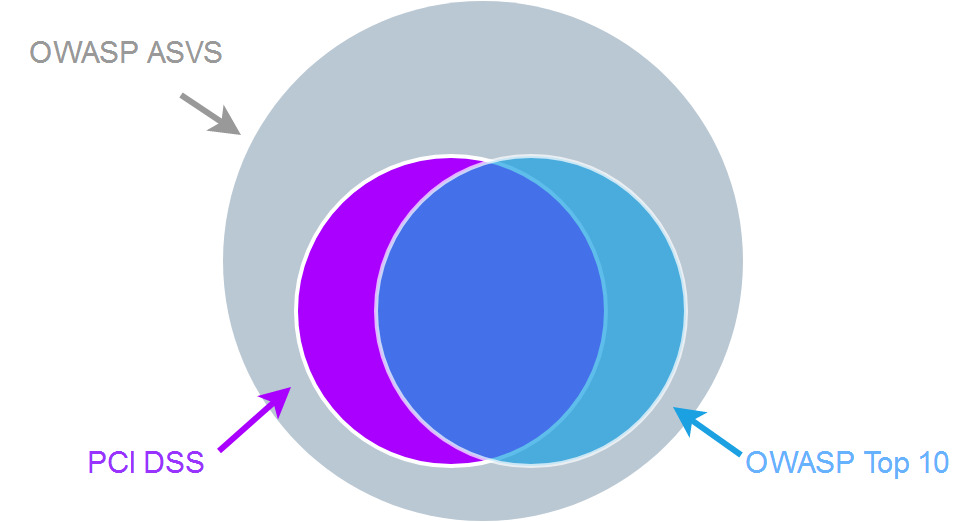
(See OWASP ASVS "Appendix D: Standards Mappings").
For What
- Case 1: To improve security of your application.
- Case 2: To carry out security assessment, penetration testing.
Below I proceed over the case #1.
One of the best ways to use the Application Security Verification Standard is to use it as blueprint create a Secure Coding Checklist specific to your application, platform or organization.
Step 1: Select the Level
The desirable level of application security.
| ASVS Levels | Meaning | Color | Notes |
|---|---|---|---|
| Level 3 | Advanced | The highest level. Everyone wants to get here. | |
| Level 2 | Standard | Standard. "Adequate". | |
| Level 1 | Opportunistic | You still have no security, but at least you read the yellow columns in the document | |
| Level 0 | Cursory | "Flexible", "customized by each organization", you know what it means: you have no security, byatch! |
ASVS contains recommendations how to select the level. For instance, all network accessible applications should meet the level 1 at least, and the highest level 3 is suitable for payment, healthcare equipment, for protecting trade secrets.
Let's consider "V1. Architecture, design and threat modeling":
- Level 1: all components are well-known (identified).
- Level 2: Level 1 + implementation is good.
- Level 3: Level 2 + meta requirements are met, threat model exists, architecture is drawn, everything is defined, described, identified etc.
Of course, a higher level is better for security, but implies much more efforts to achieve.
Step 2: Follow the Check List
Select the level, follow the color.
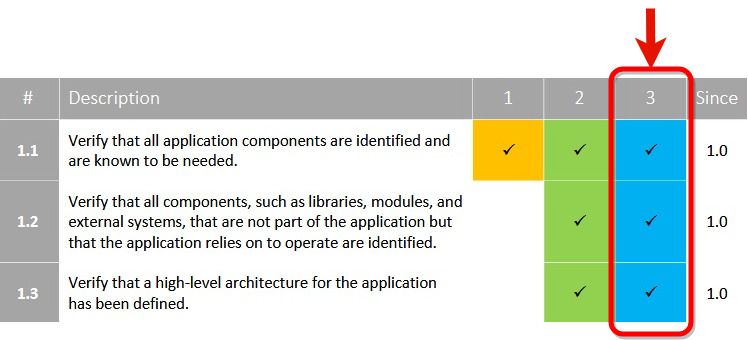
Go through all chapters.
- V1. Architecture, design and threat modeling
- V2. Authentication
- V3. Session management
- V4. Access control
- V5. Malicious input handling
- V7. Cryptography at rest
- V8. Error handling and logging
- V9. Data protection
- V10. Communications
- V11. HTTP security configuration
- V13. Malicious controls
- V15. Business logic
- V16. File and resources
- V17. Mobile
- V18. Web services
- V19. Configuration
Step 3: Share the Report
The report can be used internally or publicly as a result of compliance control (like PCI DSS).
Application Security Verification Report is a report that documents the overall results and supporting analysis produced by the verifier for a particular application.
The End
ASVS is written in a pretty straightforward comprehensive way, has a simple structure, and helps you to do your work: you go through the check list, assess a software, report to stakeholders, improve security.