Mobile App Security Testing: Tips, Notes, iOS/Android
Mobile application threat model. Tools to conduct a security analysis: mitmproxy, frida, jadx-gui, mobsf, apktool, r2, etc.
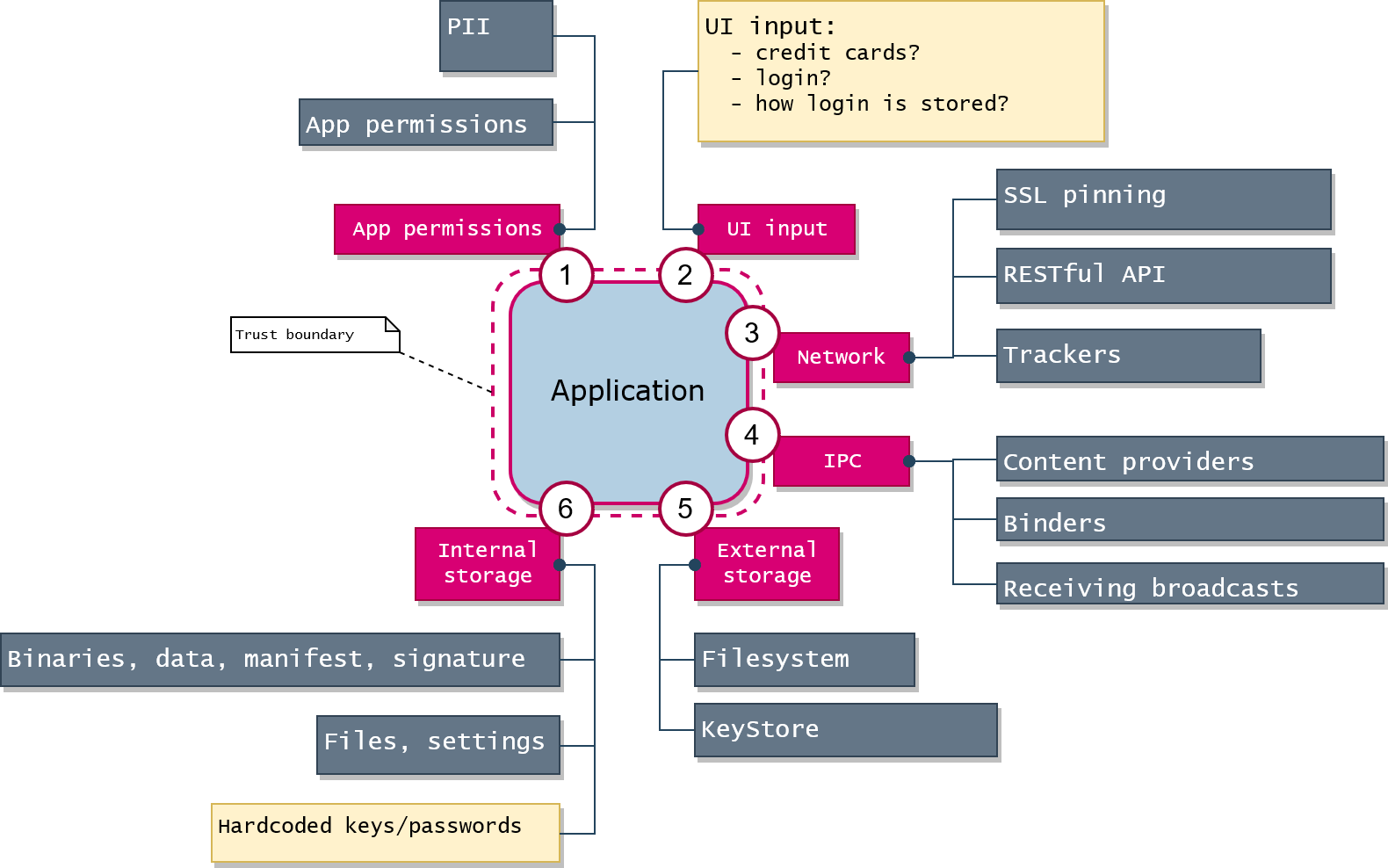
When you don't know where to start, start from a threat model. I think about any application in a way like the following:
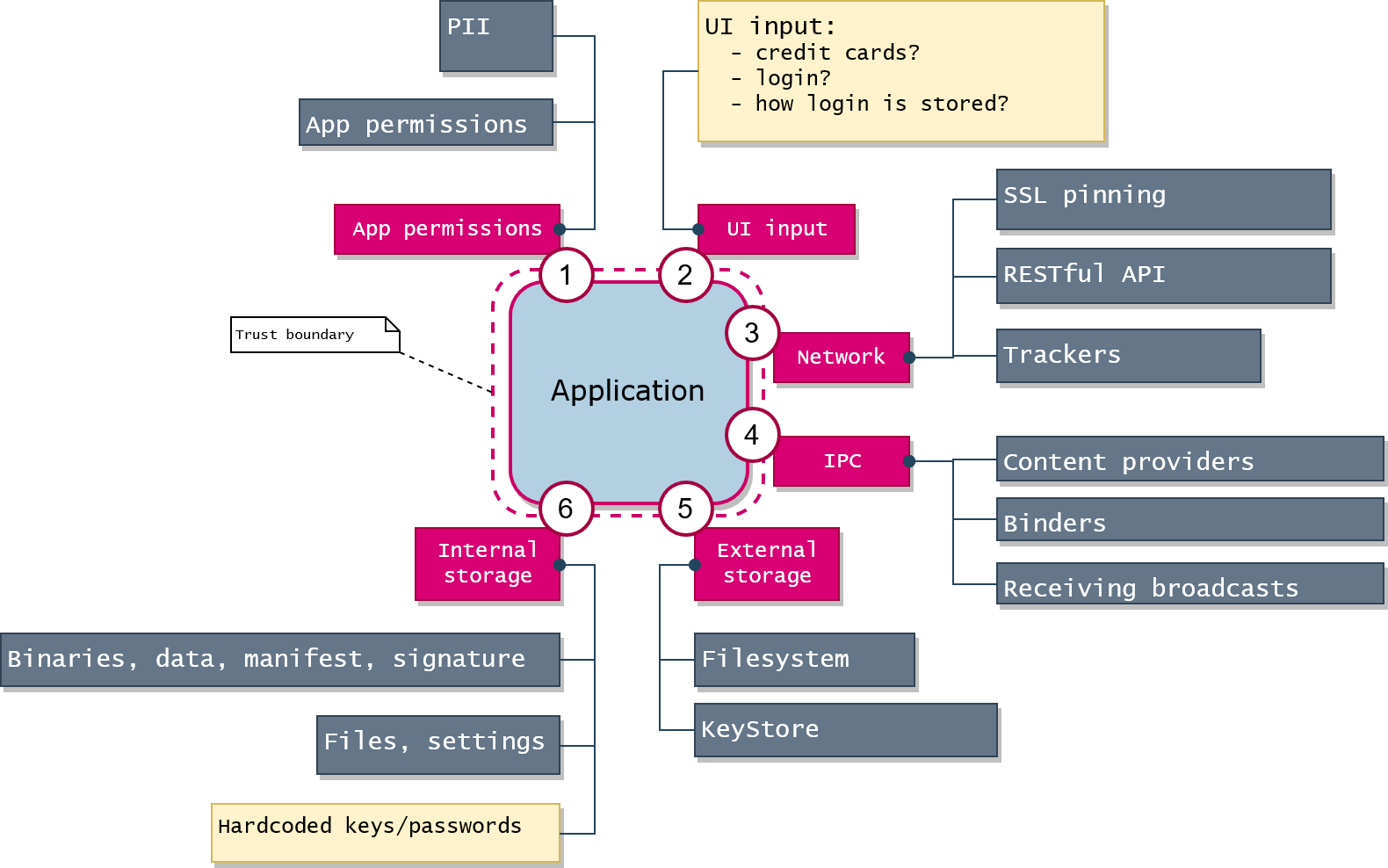
A threat model can be any comfortable to you.
If to imagine any application as a black box, the imaginary boundary could be drawn around the box: the external perimeter where the data flows from/to the outer world.
Static analysis ("grepping") will give you some initial basic ideas: just use grep to find 'http://' links, passwords or any suspicious stuff. Basically, such frameworks like MobSF gives you a lot of info (but not enough) about APK on the initial step of Android application analysis. Application permissions will give you an idea what kind of personal info the application may potentially gather.
Dynamic analysis (tracing/debugging) will give you the actual picture of what happens in the application: sessions identifier, outgoing traffic, plain data before the encryption.
Sniff HTTPS Traffic using MITM Proxy (SSL proxy)
View the traffic that the application sends to the network via HTTPS. You may need it to verify PII leaks or analyze protocols of application level (e.g. RESTful API). It's a good starting point, as you analyze the application as a black box.
⚠ Interception won't work in Android without proper MITM certificate installation. The easiest way is to modify APK, so it accepts 3rd party user certificate injection. Read the following section. 👇
Start With That: Certificate Unpinning to Intercept HTTP Requests
Even using SSL proxy you may see that some traffic cannot be decrypted, and it means that the application uses either the default system certificate storage excluding user certificates or certificate pinning for particular URLs.
- 👉Any MITM proxy doesn't work for Android applications because only system certificate storage is applied as a source of trust excluding user's MITM certificates. ❗ Modify APK to overcome this. 📝Re-sign APK with Uber APK signer.
- You may use certificate unpinning techniques to change the pinned certificate and analyze the traffic: use Frida to inject the certificate unpinning code snippet (and you don't need a root on Android for using Frida).
- Another option: reverse engineer, modify and re-pack the application putting a MITM certificate into APK instead of a pinned certificate.
- Having an Android rooted emulator you may have to modify system certificate storage there.
- You don't want to waste your time, so try to find a
TrustManagerimplementation in the case of an Android application to see how the chain of trust is configured.
iOS Application Security Testing
- Jailbreak iOS device for the further security research.
- Connect device to the same network (e.g. Wi-Fi network).
- Install Frida (https://frida.re), SSH daemon.
- Connect to device via SSH (
ssh root@192.168.0.111, login:root, password:alpine). Traverse file system using bash tools; usescpto copy some files from the phone to the host. - Install iOS application from App Store, extract IPA (iOS application package), test it with MobSF.
- Decrypt application using frida-ios-decrypt, Clutch, dumpdecrypted.dylib.
- Trace filesystem, network, encryption:
frida-trace -m "-[NSFileManager fileExistsAtPath:]" -U <pid/appname>
frida-trace -m "-[NSURLSession dataTaskWithRequest*]" -U <pid/appname>
frida-trace -i CCCrypt -U <pid/appname>Android Application Security Testing
- Test APK with MobSF: https://github.com/MobSF/Mobile-Security-Framework-MobSF. MobSF gives much more insights about Android app than about iOS app.
- Unpack
classes.dexfrom APK file, usegreplooking for http links, password, key, paths. - Use jadx (
jadx-gui) to decompile APK (just skip d2j-dex2jar tool cause it's pretty outdated nowadays). - Use Frida (https://frida.re). To avoid rooting, use
frida-gadget: it's is the library which you have to insert into APK, re-pack/re-sign and thenadb install -r you-self-signed-with-gadget.apk. Then run application and thenfrida-trace -U Gadget. - Look into
libs/subdirectory of APK: if there are native shared libraries inside, then you may usestrings libblabla.so | grep passwordandr2 libblabla.soto do some reverse engineering using Radare2 (or use IDA, but it's not free). - Many of the tools above use
apktoolunder the hood. I would recommend to install the version 2.4.1 and higher to save your time catching the errors related to the older versions.
Use OWASP MSTG to Get More Ideas
It is here: OWASP Mobile Security Testing Guide